Google Confirms New Attack Can Read All Gmail Messages: Iran Accounts Targeted
For almost 10 years, the Iran-backed threat actor, sometimes referred to as Charming Kitten, has been causing a stir in the cyber threat arena.
The threat group is famous for launching malicious campaigns against government and military personnel, journalist, and scholars in the U.S. and the Middle East.

Google Confirms New Attack Can Read All Gmail Messages Iran Accounts Targeted
While Charming Kitten might not be the most advanced state-sponsored APT35 group in the world, its offensive toolkit is sophisticated and effective.
Recently, researchers discovered a custom data exfiltration tool launched by the Iranian cyber-espionage group dubbed HYPERSCRAPE. According to a report by Google’s Threat Analysis Group (TAG), the tool infects the victim’s device to steal data from users of Gmail, Microsoft Outlook, and Yahoo accounts.
What is HYPERSCRAPE, and How Does it Work?
Although Google TAG cybersecurity researchers detected HYPERSCRAPE in December 2021, the tool has been under active development since 2020.
It’s a custom malware written for Windows systems in .NET. The program uses a spoofing technique to disguise itself as an outdated web browser. As a result, the tool uses the Basic HTLM view feature from Gmail to view see inboxes.
Once installed on a device, it gives the attackers access to a victim’s valid email credentials or session cookies. Using these, the attacker can automatically download every email it finds in the Gmail Inbox and other mailboxes.
After that, the program set the compromised emails to unread status again. If there are any warning messages from Google, they get deleted immediately.
Google researchers also observed that other versions of the malware allowed attackers to export sensitive users’ data from the Google Takeout feature as a downloadable archive. Although Google removed the feature, it allowed customers to download data from Google services like Google Calendar, Doc, Gmail, and others.
The researchers noted the hacking tool functionality might vary for Microsoft and Yahoo accounts. It also won’t launch unless in a directory with other file dependencies.
Since the launch of this tool, Charming Kitten has successfully compromised dozens of mailboxes for Iranians. Luckily, Google had notified affected Gmail users through their Government Backed Attacker Warnings and taken steps to restore their accounts.
What Threat Does HYPERSCRAPE Pose?
Today, the world is in a state of perpetual cyber warfare. Over 64% of governments and their officials believe they have been victims of state-sponsored cyberattacks. Sadly, about 64 percent of security leaders, state officials, and even journalists believe they’d never notice if such hacker groups hack them. But without a doubt, many individuals and businesses can suffer huge losses if pawned by such actors.
Charming Kitten and other government-backed cyber-espionage groups are now considered the biggest threat to government organisations and institutions alike. Not only do they drive the mother country’s online geopolitical goals, but they also steal sensitive data and cripple their opponent’s defense systems and infrastructure. And the worst part is? No one is safe, and there are no government or military methods for shielding everyone.
Like many malware, HYPERSCRAPE posses a very serious threat to those targeted. As for now, it seems the group is still working on the programs because they have compromised only a handful of users (most based in Iran).
Furthermore, this exfiltration tool appears limited in terms of its ability to operate. The attacker has to locally install the malware on the victim’s device and gain the user’s credentials. It also has dependencies, such that, if relocated from its main folder, it breaks functionality. As such, everyday users are less susceptible to malware (for now).
Despite its restrictive design, HYPERSCRAPE is still an extremely dangerous program with the potential to cause significant damage to the victim. For instance, it runs in the background, so individuals won’t even know when their Gmail accounts get compromised and accessed.
What’s more, the threat actor reverts compromised emails to their original unread state and gets rid of any warning alerts from Google. Because they don’t raise any suspicions, they can hack the victim’s email and steal sensitive personal and financial data repeatedly.
For this reason, Google made the discovery of the tool public to raise awareness. This way, high-risk individuals, organisations, and government institutions can take steps to protect themselves.
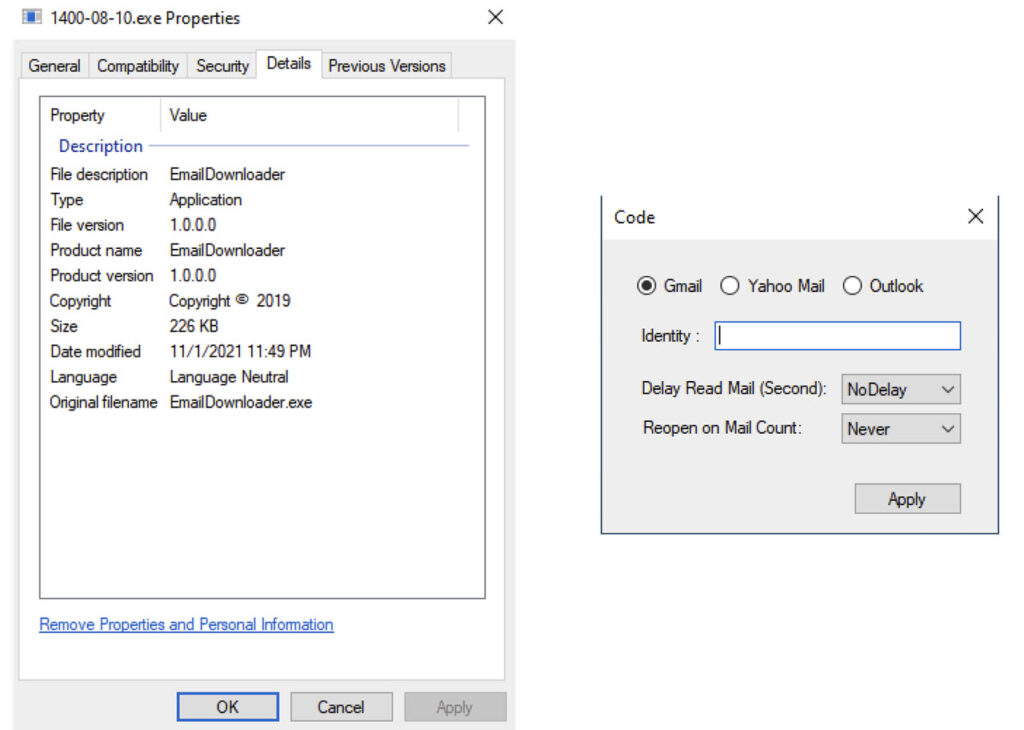
HYPERSCRAPE tool use.
How To Protect Against HYPERSCRAPE and Other Gmail Attack Threats
As said earlier, attackers can only use HYPERSCRAPE when in possession of the victim’s valid email credentials or session cookies.
So, it’s wise to always disconnect from your mailbox when you’re not using it. This way, you can reduce the time of validity of the session cookies attackers may have access to. Google also encourages high-risk individuals to join their Advanced Protection Program (APP) and leverage Google Account Level Enhanced Safe Browsing.
Gmail, Yahoo, and Microsoft Outlook account holders should enable multi-factor authentication (MFA) for their accounts. You should ensure the attackers cannot access the second mode of authentication, even if when your device gets compromised. You should also create strong passwords and avoid using the same passwords for all your accounts.
Finally, don’t forget to keep all your operating systems and software updated with the latest security patches to get rid of existing vulnerabilities.
In conclusion, HYPERSCRAPE might not possess the sophistication of most malware, but it’s notable for its effectiveness. Because of this, Charming Kitten has been able to meet its goal of accessing victims’ data, including bank accounts and personal data. But you can avoid all this mess by avoiding opening suspicious attachments and links, only using a secure website, enabling MFA, creating strong passwords, and updating your OS and software.
References
- https://www.forbes.com/sites/daveywinder/2022/08/23/gmail-hacked-google-says-new-attack-can-read-all-email-messages/?sh=3317cd10468a
- https://mybroadband.co.za/news/security/457683-iranian-malware-steals-user-data-from-gmail-yahoo-and-microsoft-outlook.html
- https://socprime.com/blog/hyperscrape-detection-iranian-cyberespionage-group-apt35-uses-a-custom-tool-to-steal-user-data/
- https://www.pcrisk.com/removal-guides/24686-hyperscrape-malware
- https://darktrace.com/blog/apt35-charming-kitten-discovered-in-a-pre-infected-environment
Written by The Original PC Doctor on 23/9/2022.