Wireless Attacks And Their Types: Here’s What You Should Know
While there is a large focus on cybersecurity threats related to the corporate world, it is important to note that consumers are also affected by these criminal activities. One report found that 85% of consumers have concerns related to cyberattacks. In another survey, it was found that a large number of individuals have experienced cyberattacks where personal information was stolen in the past. One of the biggest concerns today is the fact that the average consumer often does not have a thorough understanding of the attacks that they might face.

In this post, we are going to focus specifically on wireless attacks. These attacks have increased in the past few years and can affect consumers at unexpected times. We will consider the different types of wireless attacks affecting consumers to ensure you are better prepared and understand what to expect in these situations. These attacks affect consumers and can cause problems in businesses that are not adequately protected.
What Are Wireless Attacks?
Many people are moving away from wired network connections due to the inconvenience that comes with the use of networking cables. The move to wireless networks is convenient in both residential and commercial settings, but it brings about new risks that you need to be aware of.
Wireless attacks refer to cyberattacks that expose the Wi-Fi network used in a specific location. When cybercriminals gain access to the Wi-Fi network, they can often also retrieve private data stored on the computers and other connected devices. This can lead to the exposure of confidential information, which results in problems like stolen money and identity theft. In a corporate setting, a cyberattack that gains access to a Wi-Fi network may leak client data or other business-related data that may cause problems in the future.
Common Types Of Wireless Attacks
There are different types of wireless attacks that cybercriminals utilize in order to expose a Wi-Fi network. Each type of attack that they use has a specific range of risks associated with it. This is why consumers and corporations need to ensure they are aware of these attack types they may face over time.
We will take a closer look at the different types of wireless attacks you should understand and protect yourself against below.
SMiShing
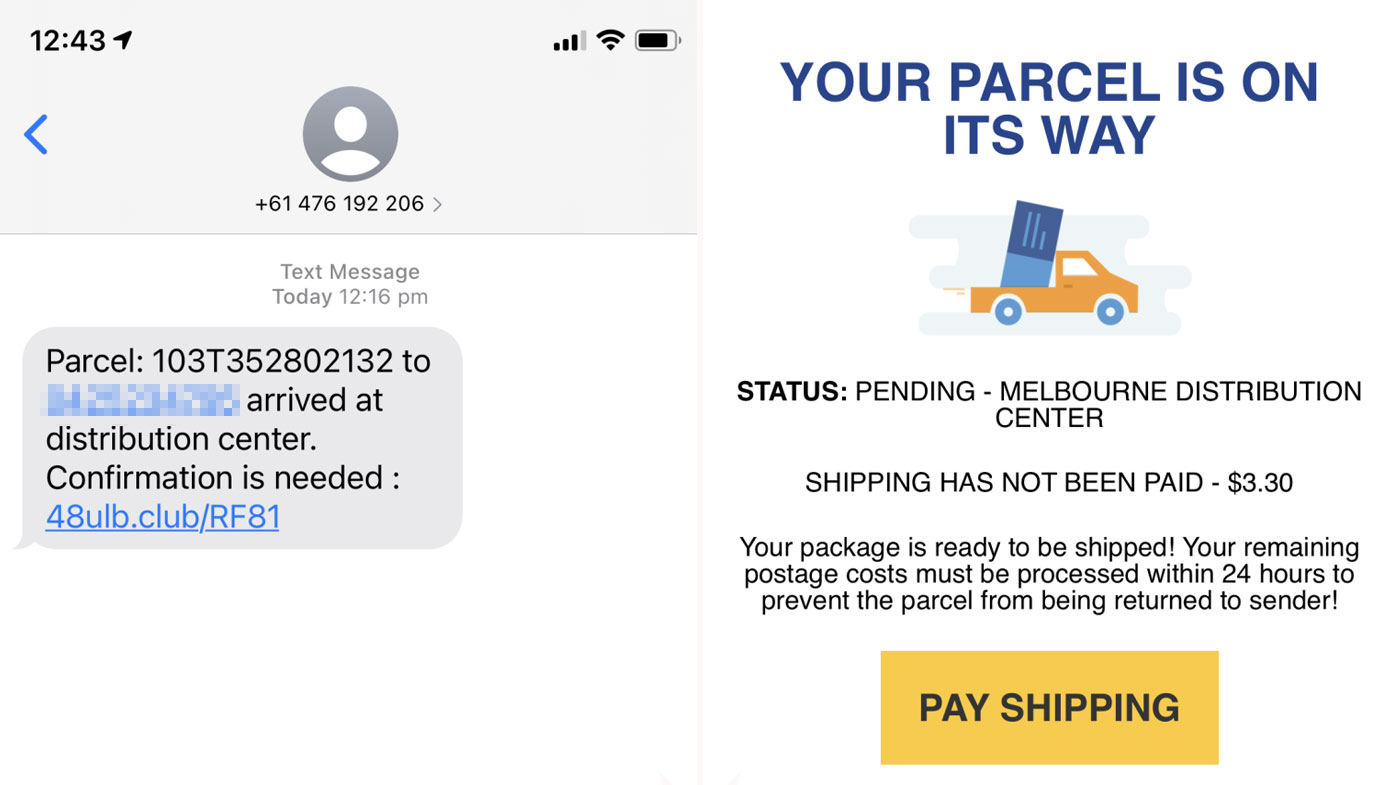
SMiShing example. Image source: 9News
A very common type of wireless attack that people face is known as SMiShing. This particular type of wireless attack generally focuses on smartphone users. Statistics show that there are about 3.5 billion people who use a smartphone regularly globally. There are different ways in which cybercriminals use SMiShing.
A common method that is used with SMiShing is the use of a short message service, also known as an SMS. The SMS may contain a link that infects the recipient’s smartphone, which can then allow the cybercriminals behind the attack to gain access to confidential data stored on the phone through its wireless internet connection.
WEP Attack
Another relatively common attack type includes accessing a network by bypassing the WEP security module that is installed on the router. WEP is a type of security protocol that helps to protect against unauthorized access, also known as Wired Equivalent Privacy.
The main idea behind WEP is to provide a similar level of protection as a LAN connection offers. The WEP technology encrypts data with a key, which is shared among all users that are connected to the Wi-Fi network. This gives the cybercriminal access to a variety of user accounts with encryption keys that they can monitor in order to find a hole in the network security.
Bluejacking

Bluejacking the mobile via bluetooth. Image source: MSPoweruser
Bluejacking is not as common as some of the other wireless attacks noted in the modern day, but still, something that people should be aware of. This particular type of attack often affects the consumer, particularly due to the short range of Bluetooth transmissions. Bluejacking involves submitting an unauthorized message to another device through a Bluetooth connection. These messages may contain harmful software that invades the user’s smartphone and gives the criminal access to the information stored on the device.
In addition to Bluejacking, it is also important to consider Bluesnarfing. This is a type of wireless attack that also involves a Bluetooth connection. What happens with Bluesnarfing is the criminal will copy data from the victim’s smartphone over to their own device. This can include various data, including the contact list, calendar entries, text messages, and even e-mails received on the victim’s phone.
WPA Attacks
The majority of Wi-Fi routers use a technology known as WPA or WPA2 to enhance the security of connections on the network. These technologies have been released as successors to WEP and use different encryption methods to help prevent cyberattacks. However, there are still several cases where these attacks are noted even when the router provides WPA or WPA2 protection.
With WPA technology, cybercriminals will generally monitor traffic on the network in order to identify a way to break through the security protocol. WPA2 is a bit different, as in this case, packet data is rather monitored by cybercriminals. The criminal will monitor packet data transmitted between an authorized user and the access point itself, then look for vulnerabilities they can expose using this data.
Fake Access Points
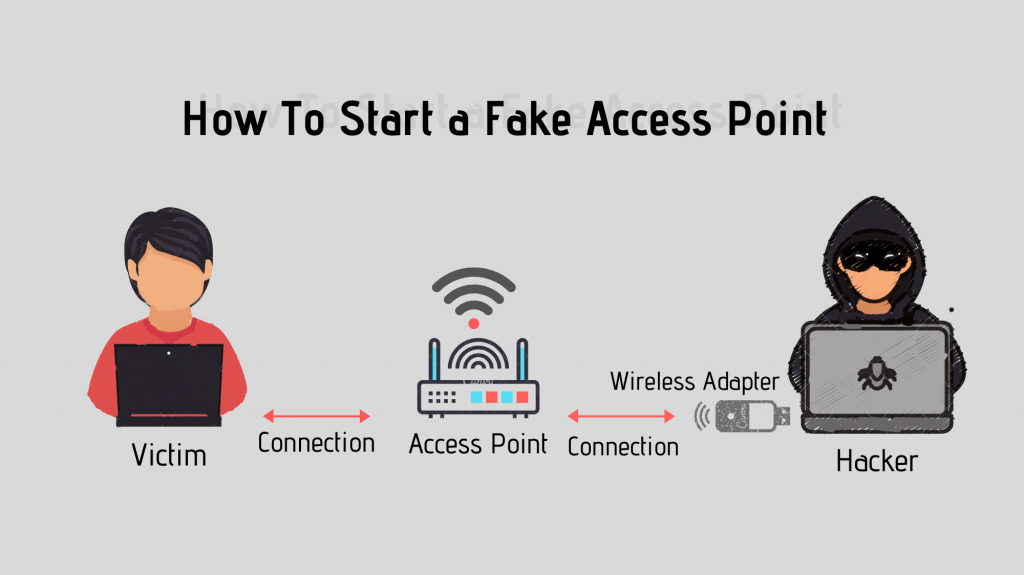
Fake Access point flowchart – Image source: zSecurity
Another common threat that people should be on the lookout for includes fake access points. When people visit restaurants or book into a hotel, they often connect to the free Wi-Fi offered by the facility. While free Wi-Fi is useful when it comes to accessing the internet, you need to look out for fake networks that cybercriminals create in the surrounding area.
These fake access points will often have a similar SSID as the facility’s network, which often makes them difficult to identify. Once a person connects to this fake access point, the attacker usually gains access to confidential data on the victim’s smartphone. This can lead to information like contact lists, emails, account data, and more being exposed and stolen by the criminals involved with the fake access point.
Protection Against Wireless Attacks
Implementing appropriate protective measures is crucial in the modern day, especially when you frequently use wireless networks to connect to the internet. There are several precautionary steps that you can take to protect yourself and a business network against these attacks.
When it comes to protecting consumer data, it is important to be wary of free Wi-Fi access points. If you do need to connect to one of these access points, always check with the provider to find the specific SSID that you should look for. It’s a good idea to only connect to free Wi-Fi spots that use a password. You can ask the provider for a password.
With your home network, it is important to ensure you implement appropriate security modules on the router that you use to provide Wi-Fi access. Once you set up the router the first time, make sure you change the SSID and do not use the default data that comes with the device. This can create vulnerabilities in your network. Instead, change both the default SSID and the password to add an extra layer of security to the network.
In a corporate setting, you should follow the same protocol – avoid using the default data that comes with the router. You do, however, need to implement additional security measures in a business environment, as data protection is critical. Make sure you install a network firewall system that is capable of protecting against invading users that are not authorized to access Wi-Fi connections. You also need to ensure you have firewalls and antivirus programs installed on every computer within the business that is connected to the wireless connection.
This can help to provide better coverage when it comes to keeping invaders out of your network. When an invader does gain access to the network, the individual firewalls installed on each computer can help to block them out of databases and other data that are related to confidential information.
Regular checkups and testing of your business’s wireless network are other things that you should keep in mind. You should contact an agency that focuses on cybersecurity and have them implement test attacks against your wireless network to see if there are any vulnerabilities that you need to be wary of. This way, you can address these vulnerabilities before cybercriminals are able to identify them.
Conclusion
Both consumers and businesses need to be aware of the risks involved with using wireless networks. While Wi-Fi internet access is convenient, it does bring about certain risks. Implementing the appropriate actions to provide protection against wireless attacks can help to protect confidential information, such as client data or credit card details. We looked at different types of wireless attacks that you should be wary of in this article.
References
- https://www.csiweb.com/what-to-know/content-hub/blog/what-are-financial-consumers-top-2021-cybersecurity-threats/
- https://www.isaca.org/resources/news-and-trends/isaca-now-blog/2022/the-impact-of-cybersecurity-on-consumer-behavior
- https://techjury.net/blog/smartphone-usage-statistics/
Written by The Original PC Doctor on 21/1/2023.