CISOs Report That Ransomware Is Now the Biggest Cybersecurity Concern and What Are the Concerns In 2022
According to CISOs, CTOs, and CIOs, ransomware is the biggest cybersecurity concern for their organisations today. This follows the surge in ransomware attacks in 2021, with ransomware demands and payments rising significantly. In fact, a report by SonicWall said over 470 million ransomware incidents got recorded over the first three quarters of 2021.

Ransomware
We can attribute the increased ransomware attacks to accelerated digital adoption and the rapid evolution of IT infrastructure in recent years. But that’s not all! The unique nature of this cyber threat makes it appealing to hackers.
Once loaded onto a user’s computer or organisation network, ransomware can encrypt drives and networks. Leaving the organisations with only one alternative: to pay the ransom payment as bitcoin (which can total millions of dollars) to get the decryption key.
Most organisations prefer paying the ransom because they see they believe it’s the fastest way to restore their network and data without major business disruptions. For this reason, ransomware remains one of the most lucrative forms of cyber-attacks for hackers.
However, there are other cybersecurity concerns on the horizon of CISOs in 2022. Join us as we discuss these concerns below.
Cloud Account Compromise
Cloud computing revolutionised the way we store data and information. Today, almost every organisation, irrespective of size, uses cloud services like Microsoft Office 365 to store its most sensitive information.
Although this new technology has reduced the cost of data storage and increased the efficiency of most businesses, it’s not free from vulnerabilities. The large volume of data stored in the cloud makes it an attractive target for some sophisticated hacking operations. What’s more, cybercriminals can access the data from anywhere in the world if they gain access to the organisation’s network, whether through brute force or spear-phishing attacks.
Over the past five years, cloud data security breaches have increased by 150%, according to IBM reports. The main reason for this surge is the lack of improper configuration, encryption, and authentication for cloud setups. So, corporations need to take the necessary steps to protect their cloud accounts and sensitive data from unauthorised access.
Phishing Attacks Get More Sophisticated
Phishing is among the most common cyberattacks because it’s easy to execute, and most people fall for it. It involves sending carefully targeted electronic messages to unsuspecting victims. The messages often include a link to a malicious website or malware attached. Whether the victim visits the website or installs the malware, the hackers will gain all the details they need to ransack their personal or work accounts.
Originally, phishing scams occurred over email, but lately, the attacks have become more sophisticated and executed via phone calls (vishing), messaging services (smishing), and social media. Some cybercriminals are taking things a notch higher by leveraging machine learning to write and distribute convincing messages, hoping the recipients will unintentionally compromise their organisation networks and computer systems.
If such attacks succeed, cybercriminals can steal user logins, credit card details, and other sensitive information that they can use to their advantage. Sometimes hackers even gain access to private databases.
Phishing scams also present hackers with an effective method to distribute ransomware, trojan malware, or other forms of damaging attacks.
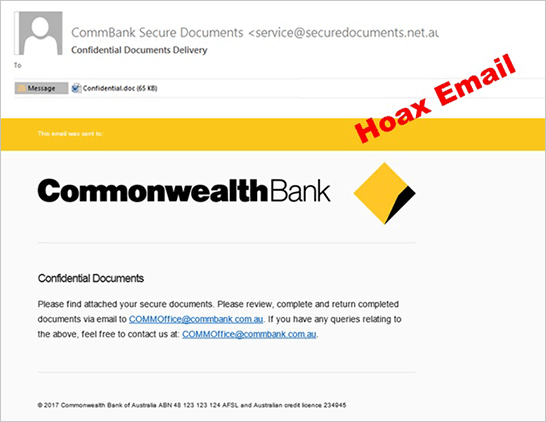
An example of phishing email – Commonwealth Bank
Business Email Compromise Attacks
Business Email Compromise (BEC) is another cybersecurity concern posing a serious threat to organisations. As a fact, the FBI named this cyberattack a “26 billion scam” that cost businesses approximately $5.01 million per breach.
According to cybersecurity researchers, cyberattack involves fraud gangs that trick enterprises into handing over money. Most of these gangs operate from Nigeria, but some run the BEC scams in the US, UK, and South Africa.
Usually, hackers gain access to a business email account and mimic the owner’s identity to defraud an organisation and its employees. They also target the company’s customers and partners. More often, the individuals who carry out the attack are part of transitional criminal organisations that employ social engineers, lawyers, and linguists.
Business Email compromise can take several forms. But in most cases, attackers will direct their efforts toward employees who have access to an organisation’s finance and try to trick them into transferring money to bank accounts that appear legit. But in reality, the money ends up in the criminals’ accounts.
The attackers can use a variety of techniques to execute the cyber-attack, including spoofing email accounts and websites, spear-phishing, and malware.
The Rise of Internet of Things (IoT) Attacks
The Internet of things is one technology that’s here to stay. Reports by Statista predict that over 75 billion devices will be connected to the IoT by 2025. That means laptops, smartphones, wearables, tablets, medical devices, automobiles, home security systems, and manufacturing equipment will communicate with each other with ease. These devices will collect, share and analyse information and generate actions.
Through connected devices, companies can collect large volumes of insightful data and streamline their business processes. Therefore, saving lots of money in the end. But this technology is not without a downside.
There have been a lot of concerns about IoT adoption. That’s because more connected devices mean more access points for cyber invasions and infections. If hackers gain control of IoT devices, they can breach personal and corporate systems, overload organisation networks, or even lock down essential equipment for financial gain.
Third-Party Exposure
Most organisations work with third-party partners, contractors, and vendors. However, a majority of third parties have no security systems or dedicated IT teams in place to prevent cyber threats. As such, attackers can hack into less-protected networks of third-party companies to access their primary target: huge corporations.
One such cyber-attack took place earlier in 2021 when cybercriminals breached SocialArks, a third-party vendor employed by Facebook, Instagram, and LinkedIn. The hackers gained access to the three companies’ networks and stole and leaked data for over 240 million accounts.
While many corporations today are aware of the potential threat third parties pose, the risk of data breaches is still very high. That holds, considering over 50% of businesses give independent contractors and other external parties access to their critical systems. Furthermore, only a few companies have placed security standards in place regarding these external parties.

Organisations need to protect their digital protection from ransomware.
How Organisations Can Protect Against Ransomware and Other Cybersecurity Concerns
With cybercriminals becoming more sophisticated and adapting their techniques to boost their chances of success, it’s proving more difficult for organisations to protect themselves. Nevertheless, there are a few strategies and practices that can give your company an upper hand against ransomware and other cybersecurity threats.
Regularly Back Up Your Systems and Data
Most cyber-attacks, including ransomware, target the organisation’s systems and data. Once hackers gain control of a company’s network, they can lock business owners and employees out of the system and hold their data until they pay a considerable sum of money.
But with backups, a company can safely disconnect the infected devices from the network, wipe them clean, reinstall backup files and rebuild the systems in a safer setting.
As a rule of thumb, always keep 3 separate copies of your data on two storage media, with one copy offline to use in the event of disaster recovery. Take things a notch higher by adding one copy on an immutable, indelible cloud storage server.
Apply Security Patches When Released
The best way to keep a company’s security system and network safe is to fix vulnerabilities that can act as back doors for hackers. Keep in mind that ransomware, viruses, and malware evolve constantly. That means new variants can bypass old security features with ease. For this reason, you need to ensure that your organisation’s operating systems, browsers, antiviruses, and other software are updated with the latest security patches.
Failure to update your systems on time can increase your company’s susceptibility to hacking risks. Also, remember once vendors announce a patch, cybercriminals are alerted to the weakness. If you don’t act first, they will exploit it to carry out attacks against your company.
While your organisation might have genuine concerns about the reliability of security patches, you need to weigh these concerns against the potential security risk of outdated software. If possible, ensure the updates get applied automatically as soon as they’re available.
Use Email Filters and Website Blocking Tools
Email phishing attacks remain one of the most effective ransomware delivery methods for hackers. Because of these, an organisation needs to implement email protection strategies, like spam filters and website blocking tools. Such practices can help reduce the chances of employees interacting with malicious websites or ransomware.
Keeping email client apps updated and using DomainKeys Identified Mail (DKIM) can also help reduce the chances of employees and organisations falling victim to phishing attacks. Furthermore, organisations can use AI and ML to train email filtering algorithms to boost the robustness of their security systems.
Conclusion
Without a doubt, ransomware remains the most damaging and disruptive cyberattack. So, it makes sense that most CISOs are concerned about its impact on their organisations. However, other cybersecurity threats like phishing, business email compromise attacks, third-party attacks, and cloud account compromise should get factored in. While these threats might not be visible as ransomware incidents, they can pose a huge problem for companies. With that in mind, taking a few basic steps like improving employee awareness of cybersecurity, implementing spam filters, and applying security can go a long way in preventing damaging attacks on the organisation.
References
- https://www.zdnet.com/article/ransomware-is-now-the-biggest-cybersecurity-concern-for-cisos/
- https://www.lepide.com/blog/top-security-concerns-for-cisos-in-2022/
- https://www.infosecurity-magazine.com/news/2022-state-industry-report/
- https://www.zdnet.com/article/microsoft-office-365-is-becoming-the-core-of-many-businesses-and-hackers-have-noticed/
- https://cybersecurity.att.com/blogs/security-essentials/cisos-report-that-ransomware-is-now-the-biggest-cybersecurity-concern-in-2021
- https://www.forbes.com/sites/mikeozanian/2022/07/18/juan-soto-contract-rejection-could-make-orioles-a-better-buy-than-nationals/?sh=2ce091d69786
Written by The Original PC Doctor on 6/10/2022.