Elevate Your Cybersecurity with The PC Doctor’s Penetration Testing Services
Unveil Vulnerabilities Before They Strike. Penetration Test Today!
In an era where digital security is paramount, The Original PC Doctor is your premier ally in safeguarding your digital assets against cyber threats. Our penetration testing, or pen testing, services simulate real-world cyberattacks on your computer systems or networks, pinpointing vulnerabilities and bolstering your defences against potential breaches.
Why Pen(etration) Testing is Critical
Cybersecurity isn’t just about preventing attacks; it’s about staying several steps ahead of them. Penetration testing exposes weaknesses in your IT infrastructure, including but not limited to:
- Weak Passwords: Simplistic passwords are an attacker’s playground. We uncover these vulnerabilities, preventing unauthorized access.
- Misconfigured Systems: A small misconfiguration can lead to significant breaches. Our tests ensure your systems are fortified and correctly configured.
- Outdated Software: Legacy software can be a liability. We identify outdated systems, mitigating risks before they become gateways for hackers.
- Insecure Web Applications: Web applications are prime targets for cybercriminals. Our expertise helps shield your sensitive data from prying eyes.
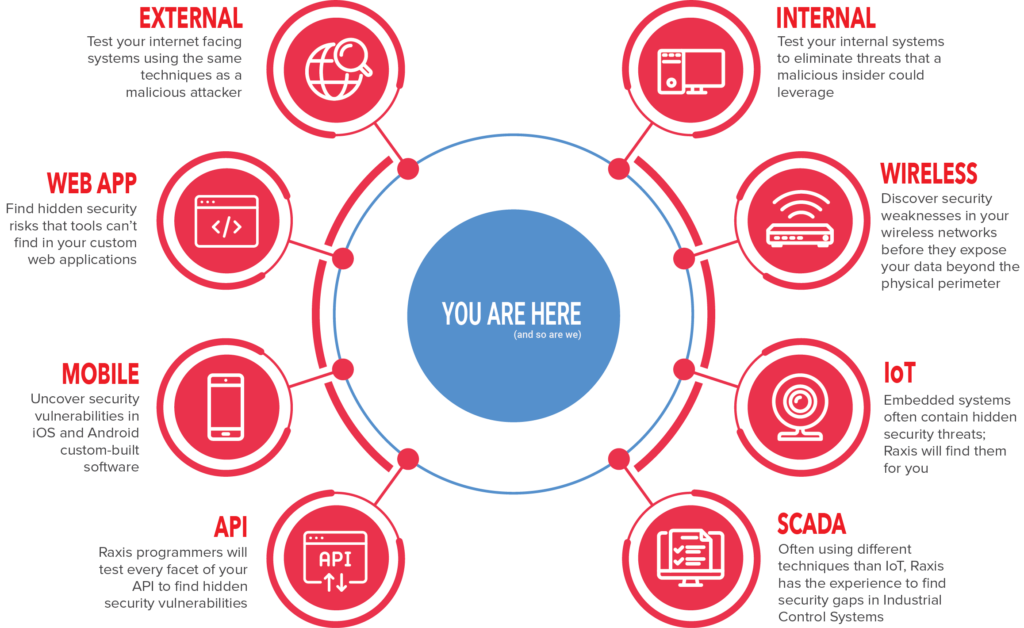
Our Penetration Testing Spectrum
Our comprehensive range of pen testing methodologies includes:
- Black Box Testing: A real-world scenario where our ethical hackers, armed with no prior knowledge, seek out vulnerabilities in your system.
- White Box Testing: With insider information about your systems, we delve deeper, uncovering hidden flaws that could be exploited.
- Grey Box Testing: A blend of both worlds, this method provides a balanced view of potential vulnerabilities, ensuring thorough security coverage.
Take Action Now – Secure Your Digital Frontier
Why Choose The PC Doctor for Penetration Testing?
- Expertise: Our team of ethical hackers uses state-of-the-art tools including Metasploit and techniques to emulate sophisticated cyberattacks, ensuring your defences are tested against the best.
- Customized Security: We understand that each business is unique. That’s why we offer tailored testing strategies, from black box to white box and grey box testing, to meet your specific security needs.
- Beyond Testing: We go beyond identifying vulnerabilities. Our comprehensive reports include actionable insights and remediation strategies to enhance your security posture.
Don’t Wait for a Breach – Act Today!
- Book Your Penetration Test: Contact The Original PC Doctor now to schedule your comprehensive penetration test. Ensure your systems are impenetrable to attackers.
- Secure Your Future: Let us help you fortify your digital assets against the ever-evolving threats of the cyber world. Our team is ready to transform your cybersecurity defences from reactive to proactive.
Transform your approach to cybersecurity with The Original PC Doctor’s penetration testing services. Secure your digital assets, protect your data, and ensure your business’s future is fortified against cyber threats.
Contact us today at 1300-723-628 to schedule your penetration test and take the first step towards unparalleled digital security.
Penetration Testing FAQ
- What is vulnerability assessment and penetration testing?Vulnerability Assessment and Penetration Testing (VAPT) are two types of analyses that are conducted to identify security flaws in a system. Although they are often combined into one process, they have different focuses and outcomes. Here’s a breakdown of each: Vulnerability Assessment: A vulnerability assessment is a systematic review of security weaknesses within an information…Read More
- What is intrusion testing?Intrusion Testing, often used interchangeably with Penetration Testing (pen testing), is a security practice designed to determine whether someone can gain unauthorized access to a system, application, or data. The key aspects of intrusion testing include the following: Purpose of Intrusion Testing: Assess Vulnerability: To identify vulnerabilities that could be exploited by an attacker to…Read More
- How to find a good penetration testing service?1. Define Your Objectives: Before starting your search, know what you want to achieve with the penetration testing. Understand whether you need a network penetration test, web application test, mobile application test, or a combination of services. Clear objectives will help you choose a provider that specializes in the specific type of testing you need.…Read More
For an elaborate definition of penetration testing, check out Wikipedia online definition which also includes the history of the Art.